Application security is a multi-layered approach that encompasses various practices, tools and processes to safeguard applications throughout their entire lifecycle. The goal of application security is to prevent unauthorised access, data breaches and malicious attacks that could compromise the integrity, confidentiality and availability of an application.
The stakes are even higher for industries like legal, financial services, and real estate, where sensitive information is handled regularly. A breach can lead to severe financial losses, legal repercussions, and significant damage to a company’s reputation and customer trust. Therefore, implementing robust application security measures is not just a technical necessity but a critical business priority.
How Application Security Works?
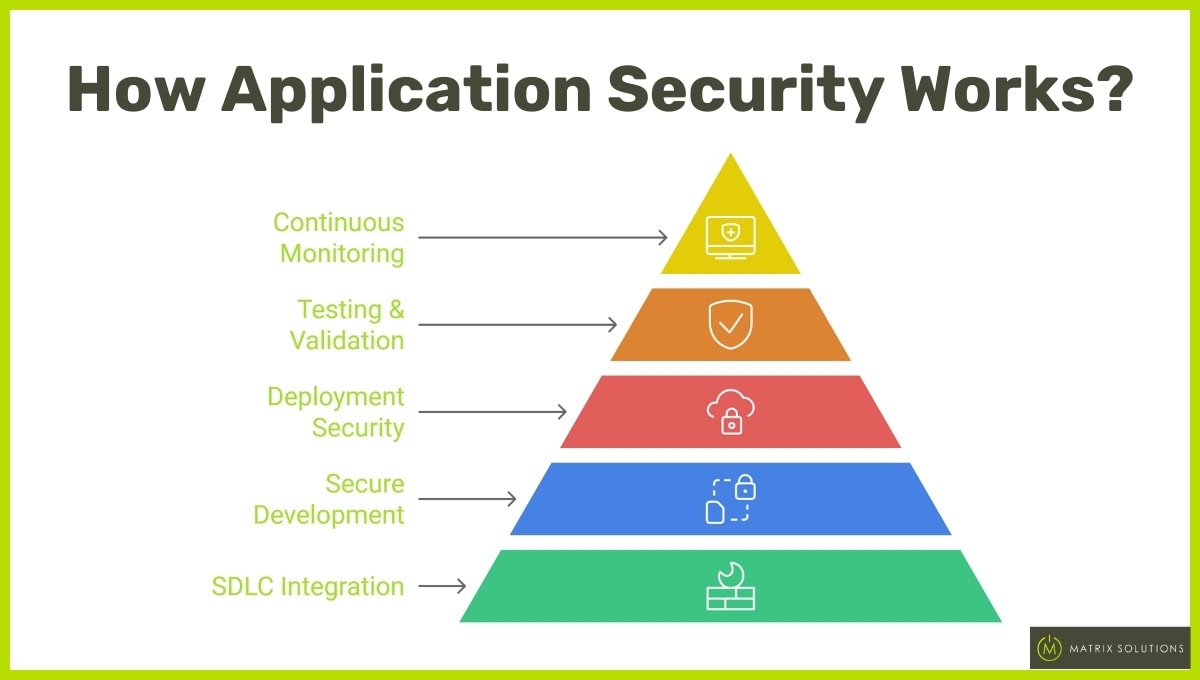
Application security is a comprehensive approach integrated into every phase of the software development lifecycle (SDLC). It begins with secure coding practices during the development phase, ensuring that common vulnerabilities, such as SQL injection or cross-site scripting, are not inadvertently introduced into the code.
Below is a detailed explanation of how application security functions effectively:
1. Integrating Security into the Software Development Lifecycle (SDLC)
- Identify security requirements during the initial planning stage. It helps in building security measures right into the application architecture.
- Implement secure coding practices to prevent common vulnerabilities such as SQL injection and cross-site scripting. Use frameworks and libraries known for their security.
- Conduct various security tests such as Static Application Security Testing (SAST) to analyse the source code for vulnerabilities and Dynamic Application Security Testing (DAST) to simulate attacks on the running application.
2. Implementing Security Measures During Deployment
- Ensure that application servers and databases are configured securely, using least privilege principles and disabling unnecessary services and ports.
- Encrypt sensitive data both in transit and at rest using robust encryption algorithms. Implement secure key management practices to protect encryption keys.
3. Continuous Monitoring and Threat Detection
- Use tools like Runtime Application Self-Protection (RASP) to monitor the application’s behaviour in real-time and block malicious activities.
- Implement comprehensive logging of all security-related events. Use Security Information and Event Management (SIEM) systems to aggregate and analyse logs for suspicious activity.
4. Regular Security Assessments and Vulnerability Management
- Conduct regular penetration tests to identify and remediate vulnerabilities that attackers could exploit.
- Use automated vulnerability scanning tools to identify security gaps in applications and their supporting infrastructure continuously.
5. Incident Response and Recovery
- Develop and maintain a robust incident response plan to quickly detect, respond to and recover from security breaches.
- Ensure that data backup and recovery processes are in place and tested regularly to minimise data loss and downtime in the event of an attack.
Importance of Application Security
Application security is essential for any organisation handling customer data, as data breaches pose significant risks. A robust application security program mitigates these risks by reducing the attack surface, making it more challenging for attackers to exploit vulnerabilities.
Decreased Disruption
Today, applications are deployed in a cloud-based environment where data flows across multiple networks and connects to remote servers, making them more vulnerable to attacks. While network security remains vital, it’s equally important to secure individual applications, as hackers increasingly target these as entry points.
When security is built into the application from the ground up, it becomes more resilient to threats, reducing the likelihood of downtime. For companies without dedicated security teams, managed service providers can offer support to maintain this level of protection, ensuring business continuity.
Early Awareness of Issues
Proactive security measures such as regular vulnerability assessments and continuous monitoring enable organisations to identify and address potential issues before they escalate. The early awareness allows businesses to respond promptly to vulnerabilities, reducing the risk of exploitation.
For companies without dedicated security teams, external experts can support these efforts by offering specialised expertise and advanced tools to maintain a vigilant security posture.
Enhanced Customer Confidence
Neglecting application security can have dire consequences, including temporary or permanent business shutdowns due to data breaches. Customers trust organisations with their sensitive information, expecting it to be kept secure and private.
A failure to protect this data can result in identity theft, financial loss and other privacy violations, severely damaging customer trust and an organisation’s reputation. Investing in the right application security solutions is significant to safeguarding both the organisation and its customers from potential harm.
Improved Compliance
Compliance with regulations such as the General Data Protection Regulation (GDPR), APRA CPS 234, and Australian Privacy Principles (APP) requires businesses to implement stringent security measures to protect sensitive data. Robust application security ensures that your business meets these regulatory demands, helping to avoid the significant fines, penalties and reputational damage that result from non-compliance.
By partnering with experienced service providers, businesses gain the necessary expertise to navigate complex regulatory landscapes. This ensures that your applications remain secure while meeting evolving compliance requirements, safeguarding your data and reputation.
Increased Cost Savings
Implementing a strong security program that includes regular testing, encryption and secure access controls is significantly more cost-effective than dealing with the aftermath of a data breach. Investing in application security during the development phase can lead to long-term savings, as addressing vulnerabilities early is typically far less expensive than fixing them after deployment.
In addition, robust application security helps businesses avoid the financial fallout of data breaches, including the costs of investigations, legal fees, regulatory fines and lost business.
Prevention of Cyberattacks
Applications are frequent targets for cyberattacks due to their accessibility and potential vulnerabilities. Common threats include malware, ransomware, SQL injections and cross-site scripting attacks, all of which can severely compromise business operations.
By adopting robust security practices—such as secure coding, regular vulnerability testing and runtime protection—businesses can fortify their applications. Proactively securing applications and continuously monitoring for suspicious activity helps organisations significantly reduce the risk of different types of cyberattacks, ensuring that sensitive data and systems remain protected.
Protection of Sensitive Data
Effective security practices, such as encrypting data and enforcing strict access permissions, are essential to prevent breaches and unauthorised access to confidential information. These safeguards help organisations protect critical assets—such as client records, financial documents and intellectual property—from tampering, disclosure or theft.
Support of Brand Image
A security breach can severely tarnish a company’s reputation, undermining years of hard-earned trust. Demonstrating a proactive approach to data protection and ensuring the integrity of services is essential to maintaining a positive brand image. By implementing robust security measures, businesses demonstrate their commitment to safeguarding client data, boosting confidence among current customers and appealing to potential clients. Prioritising cybersecurity also sends a clear message to clients and stakeholders that the organisation is dedicated to protecting their privacy and ensuring data security.
Types of Application Security Measures
There are various security measures that can be implemented to protect applications from threats. These include:
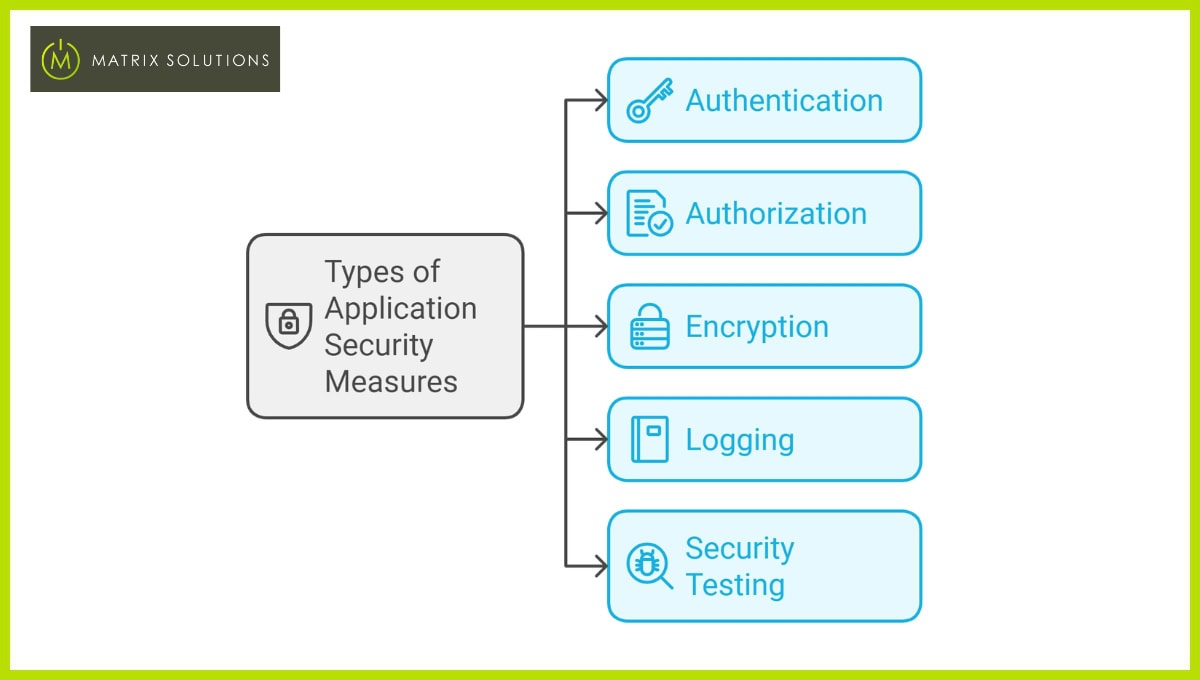
Authentication
Authentication verifies the user’s identity before granting them access to the application. Methods such as multi-factor authentication (MFA), biometrics and strong password policies help ensure that only authorised users can access the application.
Authorisation
Authorisation controls what an authenticated user can do within an application. By defining user roles and permissions, businesses can restrict access to sensitive data and functions, reducing the risk of insider threats.
Encryption
Encryption protects data by converting it into a code that unauthorised users cannot easily decipher. It is important to safeguard sensitive information both at rest (stored data) and in transit (data being transferred).
Logging
Logging involves recording activities and transactions within the application. This data is invaluable for detecting and analysing suspicious behaviour, helping to identify security incidents and improving forensic investigations.
Security Testing
Security testing, including SAST, DAST and IAST, is conducted throughout the SDLC to identify and address vulnerabilities. Regular security testing ensures that new code or updates do not introduce new security flaws.
Common Application Security Risks
Despite best efforts, applications remain vulnerable to various security risks. Awareness of these risks is the first step in mitigation.
Web Application Security Risks: OWASP Top 10
The OWASP Top 10 list highlights the most critical web application security risks that commonly affect applications in production environments. Businesses must implement strong security practices during design, development and continuous monitoring to mitigate these risks.
Key Risks from OWASP Top 10:
- Broken Access Control: Unauthorised users can gain privileged access.
- Cryptographic Failures: Insufficient encryption exposes sensitive data.
- Injection Vulnerabilities: Allows malicious code (e.g., SQL injection, XSS) to be executed.
- Insecure Design: Lacks basic security controls to defend against critical threats.
- Security Misconfigurations: Weak configurations, like default passwords or improper cloud permissions.
- Vulnerable and Outdated Components: Use of outdated or unsupported software.
- Identification and Authentication Failures: Inadequate protection for user identities and session management.
- Software and Data Integrity Failures: Integrity violations during updates or insecure CI/CD pipelines.
- Security Logging and Monitoring Failures: Inadequate breach detection and response mechanisms.
- Server-Side Request Forgery (SSRF): Exploits unvalidated URLs to access restricted resources.
API Security Risks: OWASP Top 10
APIs, which facilitate communication between software components are essential for modern applications but come with distinct security challenges. As APIs grow more widespread, they introduce unique vulnerabilities that attackers can exploit. This outlines the most critical security issues, addressing potential weaknesses in their API infrastructure.
Key API Security Risks (OWASP Top 10):
- Broken Object Level Authorisation: Exposing object identifiers without proper authorisation checks.
- Broken User Authentication: Flawed authentication mechanisms that allow attackers to impersonate users.
- Excessive Data Exposure: APIs exposing more data than necessary due to improper filtering.
- Lack of Resources & Rate Limiting: Unrestricted requests leading to performance degradation or DoS attacks.
- Broken Function Level Authorisation: Weak access control, allowing attackers to gain unauthorised access or elevated privileges.
- Mass Assignment: Allowing attackers to manipulate object properties by exploiting improper data binding.
- Security Misconfiguration: Vulnerabilities caused by insecure defaults, permissive CORS, misconfigured headers, or verbose error messages.
- Injection Attacks: SQL, NoSQL, and command injections that allow unauthorised access to data or unintended command execution.
- Improper Asset Management: Insufficient API endpoints and versions tracking leads to attacks on outdated or exposed endpoints.
- Insufficient Logging & Monitoring: Poor detection and response capabilities, allowing attackers to persist and escalate attacks unnoticed.
Application Security Tools
Various tools are available to help businesses secure their applications:
Web Application Firewall (WAF)
A WAF is designed to inspect and control HTTP traffic between a web application and the internet, safeguarding against widespread threats such as SQL injection and cross-site scripting (XSS). While a WAF plays a vital role as part of a broader security strategy, it complements other tools to create a layered defence against various attack methods. In the OSI model, the WAF operates at layer seven, acting as a protective filter against attacks like file inclusion, cross-site request forgery (CSRF) and more.
A WAF functions as a reverse proxy, shielding the server from direct exposure. Positioned in front of the web application, it examines all requests from clients before they can interact with the server, effectively acting as a defensive barrier that guards against malicious traffic from the internet.
Runtime Application Self-Protection (RASP)
RASP tools safeguard applications from within, detecting and preventing attacks as they occur by monitoring the application’s behaviour in real time. While running the application, you can see how it operates, allowing it to analyse traffic and user activity. This tool can also recognise when security flaws are being exploited, immediately terminate malicious sessions, and trigger alerts to deliver active, real-time protection, ensuring a responsive defense against evolving threats.
Vulnerability Management
Vulnerability management is a key component of securing applications, focusing on identifying, categorising and addressing software vulnerabilities to reduce the risk of exploitation. These tools scan applications for known weaknesses, including those documented in the Common Vulnerabilities and Exposures (CVE) database, ensuring that no security gaps are overlooked.
Once vulnerabilities are detected, they are assessed and ranked by severity, allowing businesses to prioritise the most urgent issues. This prioritisation enables organisations to concentrate on the most critical threats first, ensuring effective risk management. Vulnerability remediation often involves applying patches or other security updates to resolve these issues, reducing the potential attack surface and enhancing overall security posture.
Software Bill of Materials (SBOM)
A SBOM provides a clear inventory of all components, libraries and modules used in an application. It helps track vulnerabilities, particularly in third-party libraries and dependencies, ensuring no component is overlooked.
By identifying software parts with known vulnerabilities, SBOMs streamline vulnerability management and allow for quick remediation. As open-source software use grows, SBOMs are becoming essential for managing risks tied to external dependencies and keeping applications secure.
Static Application Security Testing (SAST)
SAST analyses an application’s source code to detect security vulnerabilities, enabling developers to address issues early in the development process, before deployment. By examining the internal structure of the code, SAST provides a detailed assessment of potential flaws like input validation errors, insecure references, syntax mistakes and logic errors. These are particularly valuable for identifying weaknesses in non-compiled code, but they can also be applied to compiled code through binary and byte-code analysis.
Dynamic Application Security Testing (DAST)
DAST tools evaluate an application in its operational state, simulating real-world attacks to uncover vulnerabilities that may not be visible in the source code. These tools help black box testers by analysing the application’s behaviour during execution, providing insight into potential security risks.
DAST is particularly effective for identifying issues such as query string manipulation, improper script usage, data injection, authentication flaws and memory leaks. By conducting large-scale scans that simulate various malicious or unexpected test cases, DAST tools generate detailed reports on how the application responds to these scenarios, allowing organisations to address vulnerabilities in the running environment.
Interactive Application Security Testing (IAST)
IAST combines the strengths of both SAST and DAST, offering real-time feedback on security issues while the application is running. IAST tools operate from within the application server, dynamically analysing the compiled source code and inspecting software behaviour during runtime to detect a broader range of vulnerabilities.
These tools simplify remediation by pinpointing the root cause of security flaws and highlighting the specific lines of affected code. IAST tools can assess various elements such as data flow, configuration settings, source code and third-party libraries, making them especially useful for comprehensive testing, including API security evaluations.
Mobile Application Security Testing (MAST)
MAST tools are designed to detect and address security vulnerabilities unique to mobile applications, such as insecure data storage, inadequate encryption and exposure to malicious networks. MAST tools use a combination of static and dynamic analysis techniques, as well as forensic investigations of data collected by mobile apps. These tools help organisations uncover mobile-specific risks, such as jailbreaking, data leakage and exposure to malicious WiFi networks.
Cloud-Native Application Protection Platform (CNAPP)
A CNAPP offers a comprehensive security solution for applications in cloud environments, integrating protection across both the applications and the underlying infrastructure. Acting as a unified control centre, CNAPP combines features like Cloud Workload Protection Platforms (CWPP) and Cloud Security Posture Management (CSPM) with additional capabilities to safeguard cloud-native systems.
CNAPP tools typically include identity entitlement management, API discovery and protection, and automated security for container orchestration platforms such as Kubernetes.
Best Practices for Ensuring Application Security
Implementing proven strategies is vital for maintaining a robust security posture and safeguarding applications. Below are essential best practices:
Perform a Threat Assessment
Regularly assess potential threats to identify vulnerabilities that could impact your application. Evaluate how attackers might exploit weaknesses and ensure existing security measures are adequate. Consider adding cybersecurity framework or defensive layers where necessary.
Shift Security Left
Incorporate security measures early in the SDLC to identify vulnerabilities before they reach production. By integrating security testing into development and CI/CD pipelines, you reduce the risk of delays and improve the overall security of your releases.
Prioritise Remediation Operations
Vulnerabilities should be prioritised based on their severity and the potential impact on your application. Use threat assessments and CVSS ratings to ensure critical issues are remediated first, focusing on vulnerabilities that pose the greatest risk to operational security.
Measure Application Security Results
Track and report security performance using key metrics, such as the number of vulnerabilities found and resolved. Present these results clearly to stakeholders, focusing on how your security program reduces risks and strengthens application resilience.
Manage Privileges
Limit access to applications and data based on the principle of least privilege, granting users only the permissions necessary to perform their roles. It reduces the risk of both external attacks and insider threats by restricting access to critical systems and data.
Conclusion
Application security is essential for protecting digital assets and ensuring business continuity. By understanding application security and implementing appropriate measures, businesses can defend against cyber threats, safeguard sensitive data, and maintain regulatory compliance. As cyber risks evolve, so too must the strategies and tools used to mitigate them.
For small and medium-sized enterprises (SMEs), partnering with managed IT service providers like Matrix Solutions is invaluable. Offering services such as security assessments, vulnerability management and ongoing monitoring, Matrix Solutions helps businesses proactively address security challenges, meet compliance requirements and maintain a strong defense against emerging threats.
Contact us to strengthen your application security and protect your business from evolving cyber risks.
FAQs on Application Security
Application security testing involves various techniques, such as SAST, DAST and IAST, to identify and fix vulnerabilities in software applications, ensuring they are secure against potential threats.
The three pillars of application security are prevention (implementing measures to prevent vulnerabilities), detection (identifying vulnerabilities or attacks), and response (taking action to mitigate and remediate threats).
Yes, application security is a subset of cybersecurity focused specifically on protecting software applications from threats and vulnerabilities.
Yes, secure coding practices are a fundamental part of application security, ensuring that software is developed with security in mind from the ground up.