As cyber threats like ransomware and supply chain attacks grow more complex, conducting a cybersecurity audit is essential to identifying weaknesses, evaluating risks, and fortifying defences. Whether you run a small enterprise or a large corporation, understanding how to perform a cybersecurity audit is key to protecting sensitive data and maintaining operational continuity. Below, discover actionable steps for performing successful cybersecurity audits to mitigate risks and secure your infrastructure.
What is a Cybersecurity Audit?
A cybersecurity audit is a structured assessment of your organisation’s network, server, and physical security measures. Its primary aim is to minimise the risk of cyberattacks and protect vital business and customer information. During an audit, you’ll assess your current policies, operational practices, and technical infrastructure to identify vulnerabilities. You’ll also measure compliance with industry standards and verify the effectiveness of your security controls. The ultimate goal is strengthening your defence against cyber threats and enhancing your overall risk management strategy.
Benefits of a Cybersecurity Audit
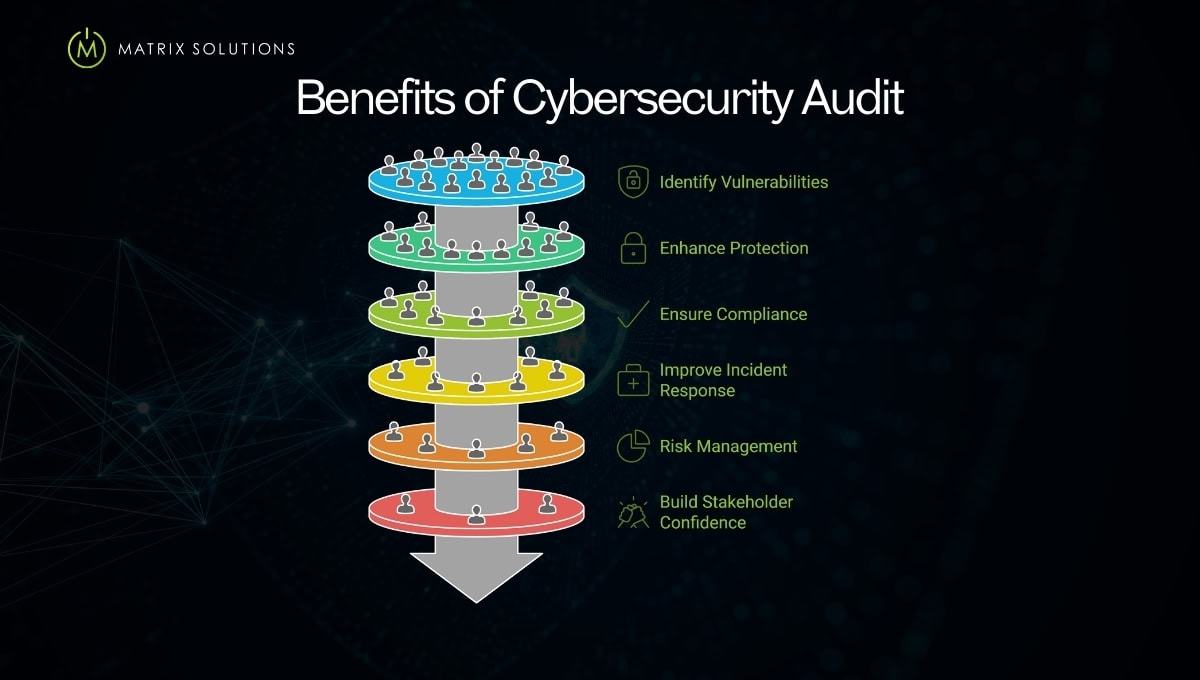
Executing a cybersecurity assessment can shield your business from threats and enhance operational efficiency. Here are the key benefits:
Identification of Vulnerabilities
A primary outcome of a security assessment is identifying weaknesses within your IT systems. Discovering these gaps enables you to proactively address and fortify them before malicious actors can exploit them.
Enhanced Protection
Identifying vulnerabilities allows for the implementation of advanced protective measures. Strengthening your defences helps guard against common threats like phishing, ransomware, and malware.
Regulatory Compliance
Different industries face stringent data security regulations. For instance, legal firms must adhere to confidentiality guidelines, while finance-related businesses must comply with standards like the Payment Card Industry Data Security Standard (PCI DSS) and Australian Prudential Regulation Authority (APRA) guidelines. Regular security audits ensure compliance, minimising the risks of penalties and damage to your reputation.
Improved Incident Response
Evaluating your incident response plan is crucial. It’s important to assess how effectively your organisation can detect, respond to, and recover from cyber threats. Improving these capabilities ensures you can quickly mitigate the impact of any security breach.
Risk Management
Comprehensive assessments reveal potential security threats, facilitating better risk management. This process helps prioritise risks and allocate resources more effectively, thus protecting critical assets cost-efficiently.
Stakeholder Confidence
Regular audits and updates to security measures build trust among investors, clients, and partners, who must feel confident that their sensitive information is secure. This trust enhances your reputation as a reliable and conscientious business.
Continuous Improvement
As cyber threats evolve, security measures must also adapt. Continuous evaluations ensure your defences keep pace with new challenges and keep your business one step ahead of cybercriminals.
How Often Should I Perform a Cybersecurity Audit?
The frequency of cybersecurity audits should align with your business’s size, nature, and industry-specific regulations. In high-risk sectors like finance, law, and insurance, conducting audits annually or bi-annually is advisable to ensure your security protocols remain robust. Here are guidelines to help determine how often you might need an audit:
- High-Risk Sectors: Annual or bi-annual audits.
- Following Significant Changes: Conduct an audit after any major system update, significant infrastructure change, or the aftermath of a data breach.
Remember, staying proactive about cybersecurity can prevent costly breaches and data loss. Regular audits help maintain compliance and bolster your defence mechanisms, ensuring your business stays protected against evolving cyber threats.
How to Perform a Cybersecurity Audit
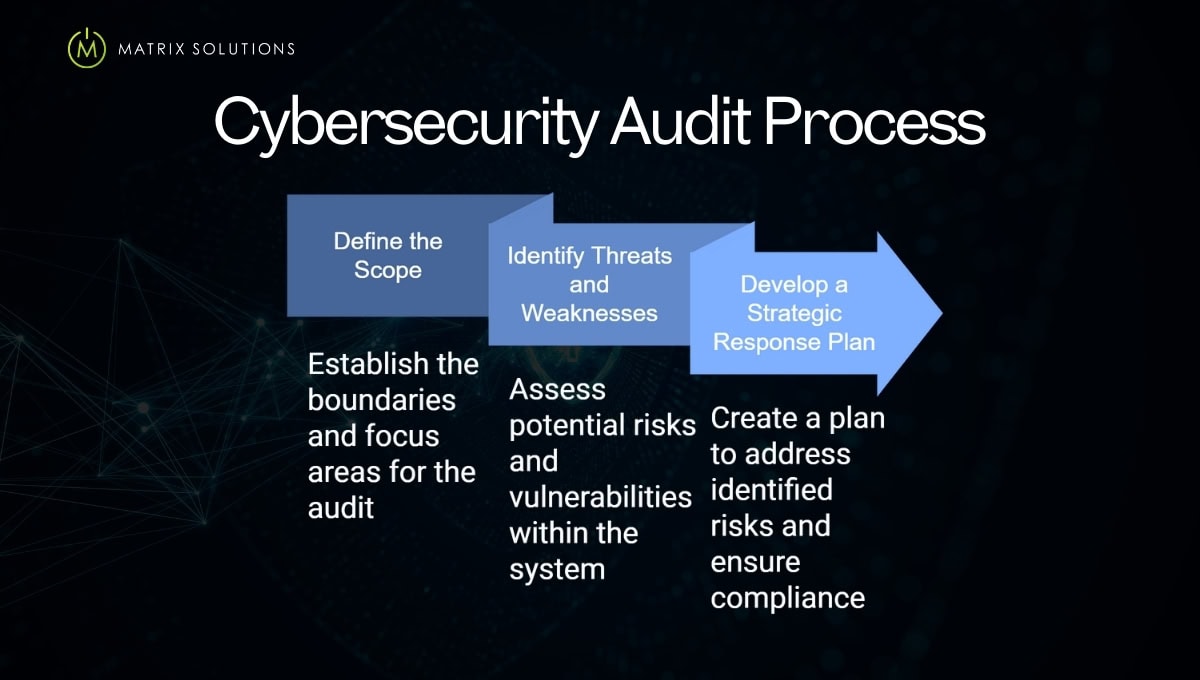
Conducting a cybersecurity audit requires a structured, step-by-step approach to ensure a comprehensive evaluation of your IT security. Below is an essential guide to the key stages involved:
Define the Scope
Begin by clearly defining the scope of your audit, which should identify the specific systems, networks, and data under review. Depending on your needs, the scope could encompass your entire IT infrastructure or target particular elements such as databases, cloud services, or security controls.
Key aspects to consider include:
- IT Infrastructure: Assess all hardware, software, and network systems.
- Sensitive Data: Examine how sensitive information is stored, transmitted, and protected.
- Physical Security: Evaluate measures to prevent unauthorised physical access.
- Security Policies: Review existing cybersecurity procedures and policies.
- Compliance Requirements: Check adherence to industry-specific regulations.
Identify Threats and Weaknesses
The next step is to identify your organisation’s potential threats and vulnerabilities. This step involves assessing external and internal risks, such as cyberattacks, gaps in employee awareness, and outdated software.
Common security threats include:
- DDoS Attacks: Risks of traffic overloads causing server downtime.
- Malware: Including ransomware threats that lock data for ransom.
- Shadow IT: Unapproved devices or apps that bypass IT oversight.
- Social Engineering: Tactics like phishing that trick staff into revealing data.
- Stolen Credentials: Risks from cybercriminals using leaked or stolen passwords.
- SQL Injections: Web application vulnerabilities that could expose databases.
- Zero-Day Vulnerabilities: Previously unknown flaws exploited by attackers.
Develop a Strategic Response Plan
After identifying risks, develop a strategic action plan prioritising critical vulnerabilities and detailing mitigation strategies. This plan should also align with regulatory compliance and include disaster recovery procedures.
A robust response plan should include:
- Risk Prioritisation: Methods to assess and address risks effectively.
- Business Continuity Measures: Protocols for rapid recovery post-incident.
- Incident Management Tools: Document detection, prevention, and response tools.
- Communication Strategy: Enhance staff training and plan for communication during attacks.
How Much Does a Cybersecurity Audit Cost?
The cost of a cybersecurity audit varies depending on the size of your business, the complexity of your IT systems, and the depth of the audit required. Generally, small—to medium-sized enterprises might expect to invest between AUD 5,000 and AUD 30,000. For larger businesses or those with intricate infrastructures, costs can escalate, particularly if ongoing monitoring and compliance are needed.
Looking for tailored advice on managing your cybersecurity investments? Contact Matrix Solutions today to explore our comprehensive cybersecurity services and ensure your business stays protected against emerging threats.
How Long Does an IT Security Audit Take?
The duration of a cybersecurity audit largely depends on its scope and depth. It takes as little as one week for smaller businesses, but larger organisations with more complex systems require several weeks to assess all aspects thoroughly. Factors such as the size of your IT environment, the number of auditable systems, and specific regulatory compliance needs can influence the timeline.
To understand what to expect for your audit timeline, consider contacting us for a detailed consultation based on your unique needs.
How Do We Conduct a Cybersecurity Audit?

Matrix Solutions have over 27 years of experience providing tailored cybersecurity solutions to legal, financial, insurance, and real estate businesses. Our comprehensive cybersecurity audit process protects your organisation from evolving cyber threats and ensures adherence to industry standards.
- Initial Consultation: We begin by understanding your business’s unique security requirements and challenges.
- Risk Assessment: We assess your IT infrastructure to identify vulnerabilities and compliance gaps, reviewing network security, access controls, and data protection protocols.
- Actionable Recommendations: After the audit, we provide a detailed report with actionable recommendations to strengthen security measures.
- Ongoing Support: Recognising that cybersecurity is a continual process, we offer ongoing monitoring and support to keep your systems secure and responsive to new threats.
Ready to protect your business with a state-of-the-art cybersecurity audit? Contact Matrix Solutions today to schedule your cybersecurity audit and take the first step towards enhanced cyber protection.