In today’s digital world, securing your business from cyber threats is more important than ever. Penetration testing helps businesses identify potential vulnerabilities by simulating real-world attacks. This proactive approach allows companies to find and fix security gaps before hackers can exploit them, making it a key strategy for strengthening cybersecurity defenses. By regularly conducting penetration tests, businesses can ensure their systems are secure, and their sensitive data is well-protected.
What is Penetration Testing?
Penetration testing, often called ethical hacking, tests a computer system, network, or web application to identify vulnerabilities that attackers could exploit. It involves simulating cyber-attacks in a controlled manner to uncover weaknesses in a company’s infrastructure. Once identified, these vulnerabilities can be addressed before malicious hackers can take advantage of them, strengthening overall security.
Why is Penetration Testing Important for Businesses?
Penetration testing is essential for businesses of all sizes because it provides valuable insights into the security of their digital assets. With cyber threats becoming more advanced, businesses must stay one step ahead to protect their operations and customer data. Regular pen tests identify weaknesses and ensure compliance with industry standards, helping build trust with customers and partners.
Identifying Vulnerabilities
Penetration testing helps uncover security gaps that might otherwise go unnoticed. By simulating real-world attacks, it identifies weak spots in systems, applications, or networks. Early detection allows businesses to fix vulnerabilities before they lead to data breaches or other security issues.
Protecting Sensitive Data
Penetration testing protects sensitive information like customer data and financial records. Security experts look for vulnerabilities that could expose this data, helping businesses safeguard it from breaches and maintain customer privacy.
Compliance and Regulatory Requirements
Penetration testing supports compliance with data protection regulations like GDPR (General Data Protection Regulation), HIPAA (Health Insurance Portability and Accountability Act), and PCI-DSS (Payment Card Industry Data Security Standard). Regular testing ensures systems are secure, preventing costly fines and reputational damage while demonstrating a commitment to data security.
Addressing Common Misconceptions about Pen Testing
There are several myths surrounding penetration testing that can prevent businesses from fully leveraging its benefits. Addressing these misconceptions is important to help companies make informed decisions about their cybersecurity. Here are some of the most common myths:
Pen testing is only for large businesses.
Cyber threats affect businesses of all sizes. Small businesses benefit just as much from penetration testing to protect their data and avoid costly breaches.
Pen testing guarantees complete security.
While essential, penetration testing doesn’t provide 100% protection. It’s part of an ongoing strategy to improve security, as no system is fully immune to attacks.
Pen testing is too expensive for small businesses.
Penetration testing is affordable for businesses of all sizes. The cost of a breach far outweighs the investment in testing, making it a valuable preventive measure.
Pen testing only finds issues with external threats.
Pen testing also identifies internal vulnerabilities, such as risks from outdated software or insider threats, ensuring comprehensive security.
Types of Penetration Testing
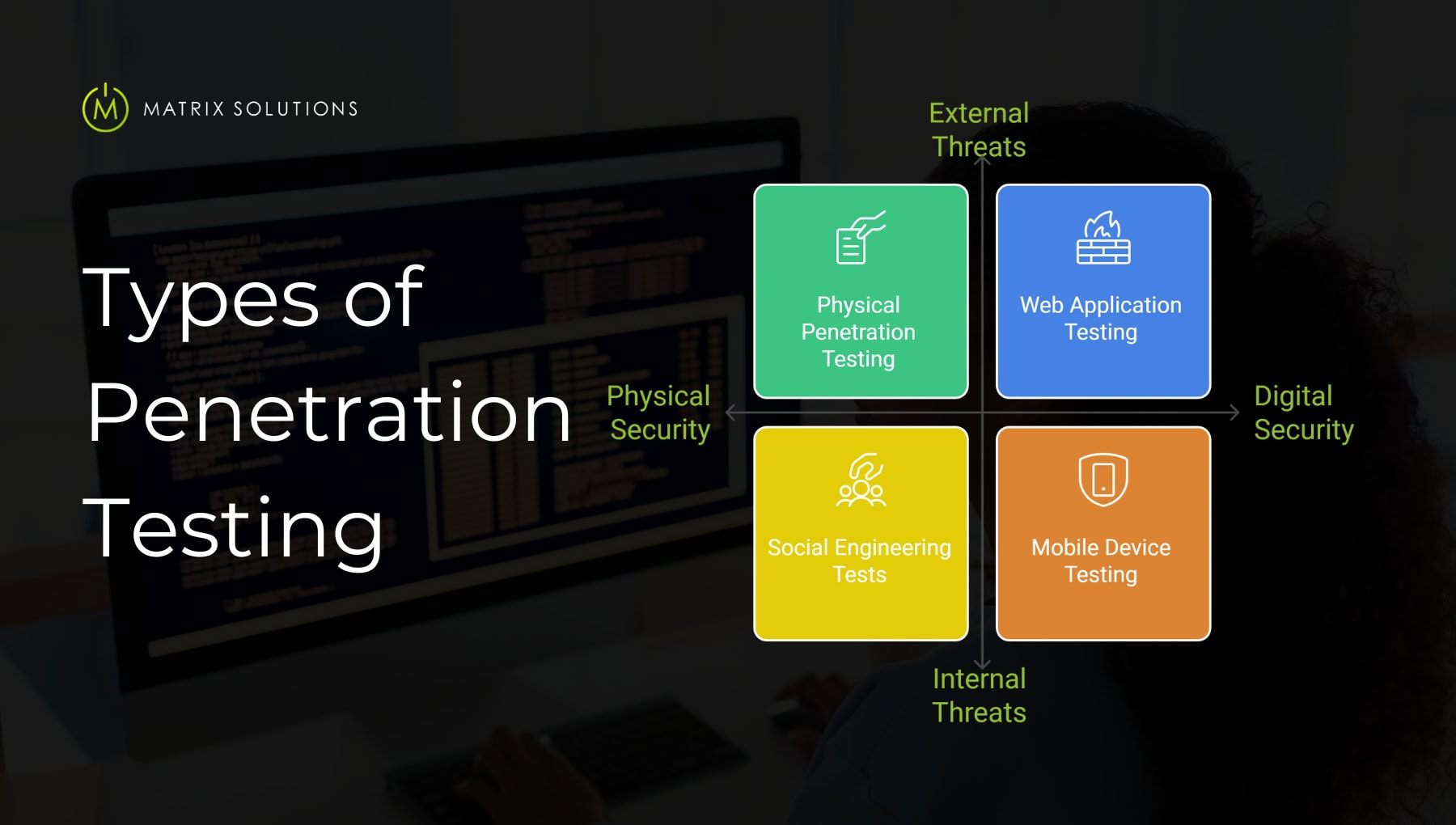
Different penetration tests focus on specific areas of a business’s security, helping protect digital and physical assets. Here’s a breakdown of each:
Physical Penetration Testing
Physical penetration testing checks for weaknesses in a company’s on-site security. Testers try to enter secure areas to see if they can bypass locks, alarms, or security checks. By finding these weak spots, businesses can better protect their buildings, equipment, and data from unauthorised access.
Mobile Device Penetration Testing
Mobile testing looks for security risks in phones, tablets, and other mobile devices. With many employees using their own devices for work, this test checks if devices or apps have security gaps that hackers could exploit. By securing these devices, companies can protect data that employees access on the go.
Web Application Penetration Testing
Web application penetration testing focuses on web apps that a company uses to run its business or serve customers. Testers check for flaws that let hackers access data, such as customer information. This test is important for any company that uses online systems, as it keeps customer data safe and secure.
Social Engineering and Phishing Tests
Social engineering tests examine the human side of security. Testers send fake phishing emails or impersonate trusted contacts to see if employees fall for them. By doing this, companies can determine how well their team recognises scams and train them to handle these threats.
These tests help build a strong, layered security approach, keeping a business safe from attacks.
Testing Approaches Used in Penetration Testing
Penetration testing uses different approaches to simulate a variety of attack scenarios. Each approach offers unique insights into potential security weaknesses, helping businesses improve their defenses. Here’s a quick comparison of these methods:
| Testing Approach | Description | Access Level | Purpose | Key Benefits for Business Security |
|---|---|---|---|---|
| White Box Testing | Tester has full access to internal information, such as code, network infrastructure, and system configurations | Full Access | Simulates an insider attack, as if a current employee or a trusted partner | Provides deep analysis of all systems weaknesses, ensuring vulnerabilities are found and fixed across the network |
| Black Box Testing | Tester is given minimal information, just like an external attacker with no insider knowledge | Minimal Access | Simulates an attack by an unknown outsider attempting to breach the system without prior knowledge | Highlights vulnerabilities that are visible to an outsider, helping to identify weaknesses in the company’s external defense |
| Grey Box Testing | Tester is given partial access, such as limited network or user-level information | Partial Access | Simulates an attack by an insider with some knowledge, like a low-level employee or a contractor | Provides a balanced assessment, testing both internal and external vulnerabilities to understand a mid-level risk scenario |
These approaches allow businesses to see their security from various perspectives, helping them build robust defenses against attacks.
How Does the Penetration Testing Process Work?
The penetration testing process involves several steps to identify and address security weaknesses. Each step builds a clearer picture of the system’s vulnerabilities and guides steps to strengthen defenses. Here’s a more detailed look at each phase:
Planning and Scoping
In this initial phase, testers and the business owner collaborate to discuss the business’s security needs. They set clear objectives, such as protecting customer data or securing a particular network, and define the scope of the test. This includes choosing which systems, applications, or data will be examined. Together, they decide on testing boundaries and requirements, ensuring the test aligns perfectly with the business’s goals.
Reconnaissance and Information Gathering
During reconnaissance, testers gather as much information as possible about the system or network they’ll be testing. This step may involve reviewing public data, analysing network architecture, and understanding how users interact with the system. The goal is to identify potential entry points and to learn how the system operates, helping testers know where to look for vulnerabilities.
Vulnerability Assessment
Once they understand the system well, testers scan it for security weaknesses. This may involve automated scanning tools that look for outdated software, unpatched systems, weak passwords, and other common flaws. The purpose is to create a list of potential vulnerabilities before any actual attempts to exploit them. This assessment helps map out which areas need improvement.
Exploitation
In this phase, testers simulate real-world attacks to see if they can exploit any weaknesses they’ve found. For example, they might bypass security measures to access sensitive data or disrupt normal operations. This step doesn’t harm the business’s actual system. However, it allows testers to understand how vulnerable areas might behave during a real cyberattack. It also reveals how much a successful attack could impact the business, potentially leading to data breaches, financial losses, or damage to its reputation.
Post-Exploitation and Reporting
After testing, the testers compile a report with all their findings. They describe each vulnerability they found, explaining how it could be exploited and the potential risks if it were left unaddressed. The report includes clear recommendations for addressing each issue, from simple software updates to advanced security measures such as implementing multi-factor authentication, network segmentation, or regular security training for employees. This phase also involves meeting with the business to review the results, answering questions, and helping plan for any necessary fixes or improvements.
Each stage in the penetration testing process helps the business understand its security status and what actions will reduce its risk. The process doesn’t just find weak spots; it offers solutions, guiding the company toward a stronger cybersecurity posture.
Best Practices for Effective Penetration Testing
To maximise the value of penetration testing, a few important practices should be followed. These steps help keep testing effective, ethical, and aligned with the business’s security goals. Here are the main areas to focus on:
Regular Testing and Maintenance
Cyber threats are always evolving, so it’s essential to perform regular and frequent penetration tests. By testing consistently, businesses can catch new vulnerabilities before they become risks. Regular maintenance ensures that new software updates, system changes, or integrations don’t create fresh security gaps.
Collaboration Between IT and Security Teams
Penetration testing is most effective when IT and security teams work together. Open communication and shared responsibility make understanding the tested systems, identifying priorities, and acting on recommendations easier. These teams can better protect sensitive data and respond quickly to potential issues by working collaboratively.
Legal and Ethical Considerations in Pen Testing
Penetration testing must follow legal and ethical standards. Before testing begins, businesses should ensure that all activities comply with regulations like the GDPR, HIPAA, and others governing data protection. Ethical guidelines should also be followed to respect user privacy and protect the company from liability. This way, businesses can build trust with their users and show a strong commitment to safeguarding data responsibly.
Following these best practices allows businesses to conduct thorough, responsible, and effective penetration testing, reinforcing their cybersecurity strategy.
Choosing the Right Penetration Testing Provider
When choosing a penetration testing provider, ensure they have the right expertise and approach for your business. By focusing on key qualities and asking targeted questions, you can find a provider to support your security goals effectively. Here’s what to look for and ask:
Essential Qualities to Look for in a Provider
- Experience: Proven success in penetration testing with a solid track record.
- Certifications: Look for certifications like CISSP, CEH, or OSCP for verified expertise.
- Industry Focus: Providers familiar with your industry will understand specific security needs.
- Responsiveness: A good provider is available and quick to support your questions and needs.
Key Questions to Ask Potential Providers
- What testing methodology do you use?
- How do you structure your reports?
- What post-test support do you provide?
- How many years of experience do you have in penetration testing?
- How do you stay updated on the latest threats?
- Can you provide references or case studies?
- What certifications do your team members hold?
Asking these questions helps ensure you choose a knowledgeable and reliable partner.
Conclusion
Penetration testing is a crucial component of any organisation’s cybersecurity strategy. It helps identify vulnerabilities, protects sensitive data, ensures compliance with industry standards, and strengthens defences against potential cyber threats. Regular testing, combined with a proactive approach to security, can significantly reduce the risk of data breaches and improve overall system integrity.
Don’t wait for a security breach to happen. Act now to safeguard your business with professional penetration testing. Contact Matrix Solutions today to ensure your systems are secure and resilient against evolving threats. Let us help you strengthen your cybersecurity and protect your valuable assets!
Frequently Asked Question - Penetration Testing
How Much Does Penetration Testing Cost?
The cost of penetration testing can vary based on the scope of the test, the complexity of your systems, and the provider’s experience. On average, a basic penetration test might cost between $3,000 to $10,000, but larger, more detailed tests can go up to $20,000 or more.
How Often Should You Perform Penetration Test?
Penetration testing should be performed at least once a year. However, it is recommended that it be performed more frequently—especially after major system changes, such as adding new applications or infrastructure. More frequent testing may be necessary to ensure ongoing security if your business deals with sensitive information or is in a high-risk industry.
Is Penetration Testing the Same as Ethical Hacking?
Yes, penetration testing and ethical hacking are closely related. Both involve simulating cyber-attacks to identify vulnerabilities in a system. The key difference is that penetration testing is often more structured and formal, typically with specific objectives and testing periods.
How Long Does a Typical Penetration Test Take to Complete?
The duration of a penetration test depends on the size and complexity of the system being tested. A basic test might take 3 to 7 days, while larger, more complex environments could take several weeks.
Will Penetration Testing Disrupt Business Operations?
Penetration testing is designed to simulate real-world attacks without causing disruption. However, minor performance issues could occur during testing depending on the test’s scope, especially in systems being actively assessed. A professional provider will work with your team to minimise any impact on your daily operations, ensuring testing is as smooth and unobtrusive as possible.
How Do You Select a Reliable Penetration Testing Provider?
When selecting a penetration testing provider, look for companies with a proven track record, industry certifications (such as CISSP, CEH, or OSCP), and experience in your specific business sector. Ask for client reference details about their testing methodologies and ensure they provide clear, actionable reports.