Managed Security Service (MSS) is a specialised third-party service that helps organisations safeguard their digital environments without the overhead of maintaining a full-fledged in-house cybersecurity team. If you’re wondering, “What is managed security services?” It’s a strategic solution that allows businesses to leverage expert skills and advanced technologies to protect against ever-evolving cyber threats. This approach benefits industries like law firms, financial institutions, and small to medium-sized enterprises (SMEs) that may need more resources to manage complex security infrastructures independently. By outsourcing their cybersecurity needs, companies can focus more on their core operations while enjoying the peace of mind of knowing their data and systems are protected round the clock.
What are the Key Components of Managed Security Services?
When considering Managed Security Services (MSS), it’s crucial to understand the core components that make up a comprehensive security strategy. These services cover multiple areas of cybersecurity, ensuring robust protection against various threats. Below, we explore the essential elements included in an effective MSS package.
Threat Detection and Response
Effective threat detection and response are pivotal in maintaining the security integrity of an organisation. Managed Security Services continuously monitor your IT environment, utilising advanced analytics and threat intelligence to detect unusual activities and potential threats. Once identified, swift and strategic responses are executed to mitigate risks, ensuring that any impact on your business operations is minimised.
Firewall Management
Firewalls serve as the first line of defence in network security, controlling incoming and outgoing network traffic based on predetermined security rules. Managing these can be complex and time-consuming. MSS providers offer expert management of firewall configurations, updates, and maintenance, ensuring that your network is shielded against unauthorised access and threats.
Endpoint Protection
Endpoint security is becoming critical as more devices, like mobile phones and remote workstations, connect to corporate networks. Managed Security Services provide strong protection for all network endpoints against malware, ransomware, and other cyber threats. This protection is regularly updated to counter new and emerging threats effectively.
Why should a business opt for Managed Security Service?
Choosing Managed Security Services (MSS) is not just about outsourcing security tasks; it’s about enhancing your organisation’s security posture with a comprehensive suite of services tailored to address specific vulnerabilities and threats. MSS providers offer continuous monitoring, advanced threat detection, and expertise, making them invaluable allies in the battle against cyber threats.
Expertise and Experience
MSS providers employ teams of cybersecurity experts with deep knowledge and experience that can be difficult to maintain in-house. These professionals are consistently trained and updated on the latest security trends, attack techniques, and defence strategies, ensuring that your organisation benefits from proven expertise.
Compliance and Regulatory Support
MSS offers numerous advantages, from significant cost savings to around-the-clock monitoring and expert compliance guidance. These benefits collectively contribute to a stronger, more secure operational environment for businesses.
Reduced Risk and Improved Security
Implementing MSS reduces the risk of cyber incidents by establishing robust security measures across your IT infrastructure. This proactive approach enhances your security posture and improves overall business resilience.
How Does Managed Security Services Benefit an organisation?
MSS offers numerous advantages, from significant cost savings to around-the-clock monitoring and expert compliance guidance. These benefits of Managed Security Services collectively contribute to a stronger, more secure operational environment for businesses.
24/7 Threat Monitoring
MSS providers monitor your systems 24/7, detecting and responding to threats in real-time. This continuous vigilance helps prevent breaches and minimises downtime, protecting your data and reputation.
Reduced IT Cost
Hiring your own cybersecurity team is expensive! MSS is a much more reasonable way to get expert protection. You save money on salaries, training, and all advanced tools required for effective security management.
Proactive Threat Detection and Response
MSS providers use sophisticated technologies to proactively detect and neutralise threats before they can escalate into serious breaches. This approach often prevents harm before it occurs.
Regulatory Compliance Assistance
MSS providers help organisations meet necessary compliance and regulatory requirements, ensuring that all security measures are up to date and reducing the risk of costly legal issues.
Vulnerability Management
Through regular assessments and proactive management, MSS providers help identify and remediate vulnerabilities within your network, thus strengthening your security defences.
Scalability and Flexibility
MSS is scalable and adapts to your business’s growth. It meets changing security needs without requiring a significant increase in internal resources.
Improved Incident Response
With MSS, your organisation benefits from enhanced incident response capabilities. MSS providers can quickly mobilise specialised teams to address security incidents, minimising the impact on business operations.
What are the Types of Managed Security Services?
MSS offers a range of solutions to cover various aspects of cybersecurity. From monitoring to proactive threat detection, each service is essential for creating a comprehensive security strategy for businesses. Let’s explore the key types of MSS available:
Security Operations Centre (SOC) Monitoring
SOC teams provide real-time surveillance of your IT systems, using advanced technologies to monitor, assess, and defend against cybersecurity threats.
Managed Detection and Response (MDR)
MDR services identify and mitigate threats. The service includes monitoring, threat hunting, incident analysis, and response activities.
Incident Response and Remediation
When a security breach occurs, rapid response is crucial. This service focuses on managing the incident, mitigating damages, and facilitating a quick recovery.
Security Information and Event Management (SIEM)
SIEM technology provides real-time analysis of security alerts generated by applications and network hardware, helping organisations to identify and respond to potential security threats.
Vulnerability Assessments and Penetration Testing
These services identify security vulnerabilities in your network and test them to evaluate the effectiveness of your defenses.
Endpoint Protection and Threat Intelligence
This includes securing end-user devices like desktops, laptops, and mobile devices and using threat intelligence to anticipate and combat potential security threats.
Managed Cloud Security
Specifically designed to protect and monitor data stored in cloud environments, this service ensures that all cloud-based assets are secured and compliant with industry standards.
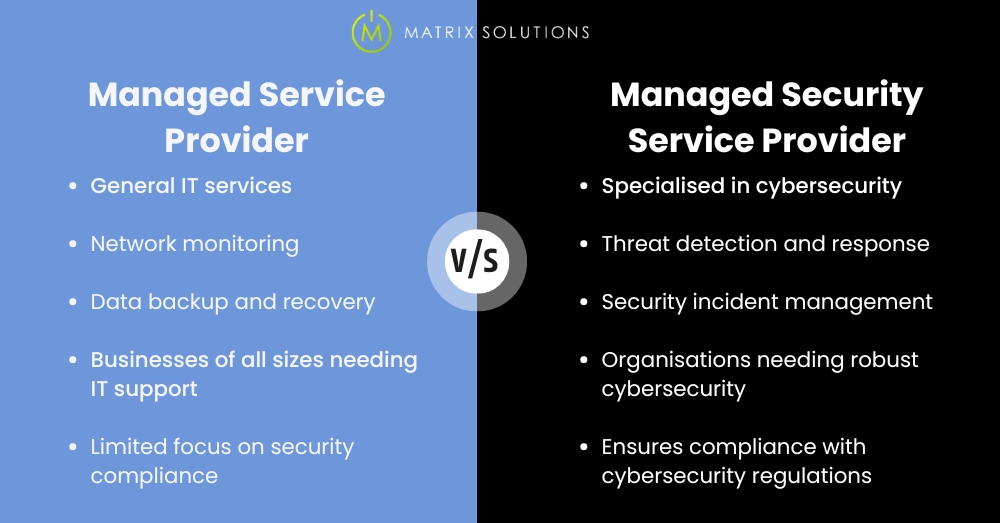
What is the difference between MSPs and MSSPs?
It’s important for businesses to understand the differences between Managed Service Providers and Managed Security Service Providers (MSSPs) to choose the services that best meet their needs. Here’s a table highlighting the key distinctions:
| Feature | MSP (Managed Service Provider) | MSSP (Managed Security Service Provider) |
| Core Focus | General IT services and support, including infrastructure management, network support, and IT consulting. | Specialised in cybersecurity services, including monitoring, threat detection, incident response, and compliance support. |
| Services Offered | Broad IT support, help desk services, hardware and software management, and sometimes basic security measures. | Comprehensive security services such as SOC monitoring, threat intelligence, penetration testing, and cybersecurity consulting. |
| Security Expertise | May have basic security capabilities but are not specialised. | High-level expertise in cybersecurity with specialised knowledge and skills. |
| Compliance and Regulatory Role | Limited role in compliance; mainly ensures IT systems work smoothly. | Proactively ensures that the client’s IT environment complies with relevant laws and regulations, focusing on security standards. |
| Ideal for | Businesses looking for broad IT support and maintenance. | Organisations need dedicated, continuous cybersecurity monitoring and management. |
This differentiation is vital for companies looking to enhance their IT and security strategies, ensuring they partner with the right type of MSSP to meet their specific needs.
How to Choose the Right Managed Security Service Provider?
Choosing the right MSSP is crucial for improving your cybersecurity. Focus on these key aspects to ensure you pick a provider that meets your security needs and business goals.
Identify Your Needs
Start by defining your specific security needs. Consider the types of threats you are most concerned about and the assets you need to protect. This will help you identify an MSSP that offers services matching your security requirements.
Assess Compliance and Regulations
Choose an MSSP that has a deep understanding of the compliance and regulatory requirements relevant to your industry. This ensures that the security measures implemented will not only protect your business but also comply with legal standards.
Evaluate Services and Technologies
Research the technologies and services offered by the MSSP. Ensure they utilise the latest security technologies and methodologies that can adapt to evolving threats.
Check Customer Support
Good customer support is essential. Your chosen MSSP should offer robust support options and be responsive to emergencies or any queries you might have.
Examine Reputation and Reviews
Research the MSSP’s reputation within the industry. Read reviews and testimonials from other clients to gauge the effectiveness and reliability of their services.
Consider Pricing and Flexibility
Evaluate the pricing structure of the MSSP. Ensure it is transparent and flexible enough to accommodate your business’s growth and changing needs without compromising security.
Analyse Security Operations Centre (SOC) Capabilities
A competent MSSP should have a fully operational Security Operations Centre that provides continuous monitoring and management of your security infrastructure.
Request Case Studies and References
Ask for case studies and references to better understand how the MSSP has addressed the needs of other businesses. This will provide insights into their expertise and effectiveness in real-world scenarios.
Why Hire Matrix Solutions as your Managed Security Service Provider?
Choose Matrix Solutions for unparalleled cybersecurity expertise and a commitment to excellence that has defined our trajectory as Australia’s top Managed IT Services Provider. With over 20 years of experience, our team offers custom solutions tailored to the unique needs of small and medium-sized enterprises. Our approach combines state-of-the-art technology with proactive service, ensuring your business thrives in today’s digital landscape. Trust us to be your cybersecurity shield, guarding against threats while you focus on growing your business.
Common Questions on What is Managed Security Services
Do Managed Security Services monitor cloud environments?
Yes, Managed Security Services include comprehensive monitoring of cloud environments to ensure data integrity and security against cyber threats.
What are Managed Security Service Providers (MSSPs) Used For?
MSSPs are used to enhance cybersecurity through services like threat monitoring, incident response, and compliance support, aligning with Australia’s essential eight strategies for cyber defense.
How do managed security service providers work?
MSSPs work by continuously monitoring your IT infrastructure, detecting threats, and responding to incidents to protect your business from cybersecurity risks.
What is mssp in cyber security?
In cyber security, MSSP stands for Managed Security Service Provider, a specialised company that provides outsourced monitoring and management of security devices and systems.
Optimise Your IT Infrastructure!
Discover the Key to Efficiency and Success With Matrix Solutions’ Managed IT Services.